Penetration Testing
The Keyu IT Services Cloud Platform gives exhaustive, ceaseless penetration testing and vulnerability scanning with noteworthy outcomes for your public cloud, applications, or organizations.

The Keyu IT Services Cloud Platform gives exhaustive, ceaseless penetration testing and vulnerability scanning with noteworthy outcomes for your public cloud, applications, or organizations.
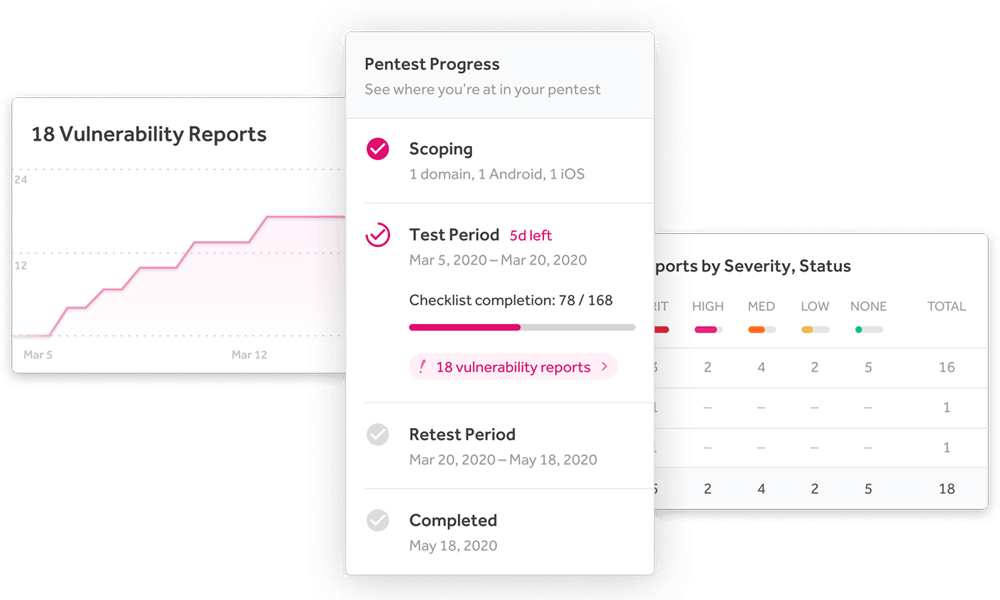
Pentests are often delivered with limited transparency into the testing process. You can track progress , discovery, testing, retesting, and remediation phases of a pentest. Pinpoint where you are in the workflow and act on vulnerabilities as they come in.
Keyu IT Services offers you the ultimate penetration testing coverage that you can manage with a click.
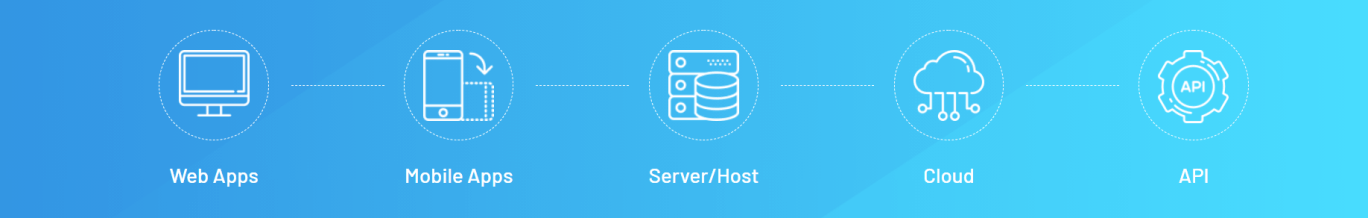

The penetration testing team detects and prioritizes security weaknesses in your IT infrastructure components and provides customers with further recommendations on how to mitigate them. They evaluate the protection level in your IT environment both with automated scanning tools and manually.

Penetration testing engineers check the protection of your entire IT infrastructure or applications to find and try to exploit security vulnerabilities, and define the measures to mitigate them.

Keyu IT Services penetration testing team combines manual checks with automated tests to verify your applications’ code security. Ketutech penetration engineers strive to identify encryption, buffer overflow, XSS vulnerabilities, and other security weaknesses possibly overlooked in the development phase and provide you with actionable recommendations to close the security gaps in your application code.

The penetration team performs an end-to-end check of your IT environment to find security vulnerabilities in:
penetration policies and procedures.
penetration monitoring tools.
Physical access control.
Configuration management.
Version control and user practices.